How T-Suite Applications protect your data in a Multi-User Environment
Background
T-Link and T-Sched have long allowed their data path to be on a shared network drive, allowing network users to access the data for reporting and analysis, and facilitating system backup.
T-Suite 2.2 introduces Full Multi-User Locking
A combination of application level and file level locking manages the processes to keep the network data safe, but still allow network user access to data retrieval and reporting.
How is T-Suite Locking Enabled?
Locking is disabled when you first install T-Link 2.2.
You can enable locking in T-Options, under Path Options on the Data Sharing Tab, by clicking Data Path is Shared:
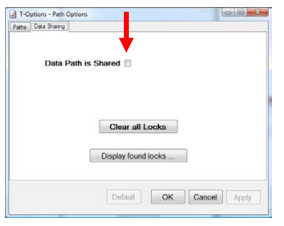
If you move your Data Path, Data Sharing is automatically set:
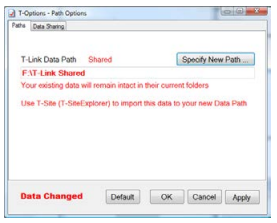
You can turn this off if the location is not shared, see below.
When T-Link, T-Sched or any other T-Suite Application is run and other locking activity is found, Sharing is enforced whether you have set the Data Path is Shared flag above or not. If you go into T-Options, this fact will be displayed like this:
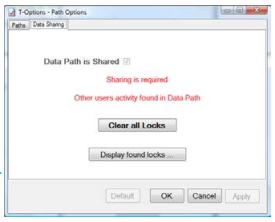
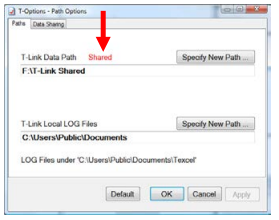
The red Shared indication is always visible on the Paths page if the Data Path is Shared for any reason.
As shown, the Local LOG Files path is also visible after the T-Link Data Path is moved.
How do you Turn off Locking?
Clear the Data Path is Shared tick box to turn off locking:
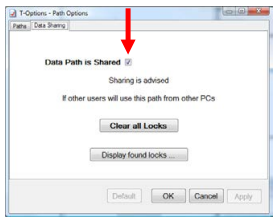
If Sharing is Enforced (as shown above) you will have to Clear all Locks before you can turn off Locking.
Clearing all Locks
Click the Clear all Locks Button to clear all currently active locks, and release the enforced sharing. You will be prompted like this to confirm this action:
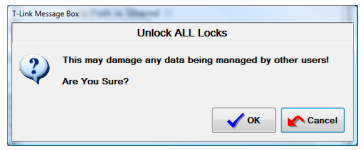
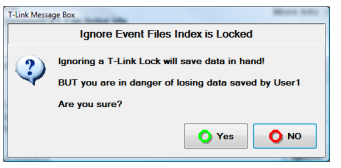
■ This can lead to damaged or lost data
This message means that if you Clear all Locks, and another user is currently depending on these locks you may cause damaged data!
You can use the Display found locks button to check who else may be using this Data Path:
Display found Locks
Click the Display found locks button to display currently active locks, like this:
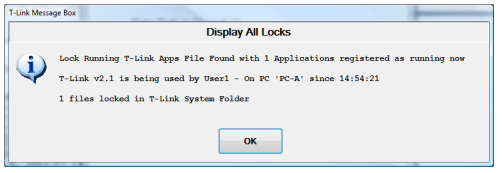
Here you are told there is one active user, and one active file lock. Any Running TLink Apps indicate possible data damage if locks are cleared.
If no locks are currently active this message will look like this:
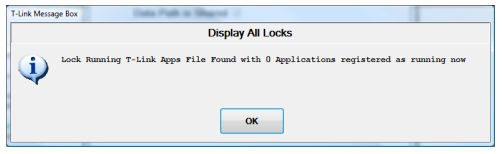
It is safer to Clear Locks in this situation, but if another user starts after you do this data loss can still occur!
■ It is best to leave locking enabled in remote paths
How will I see T-Suite Locking in Action?
T-Suite Locking applies at two levels:
- Application Locking
- File Locking
Application Locking
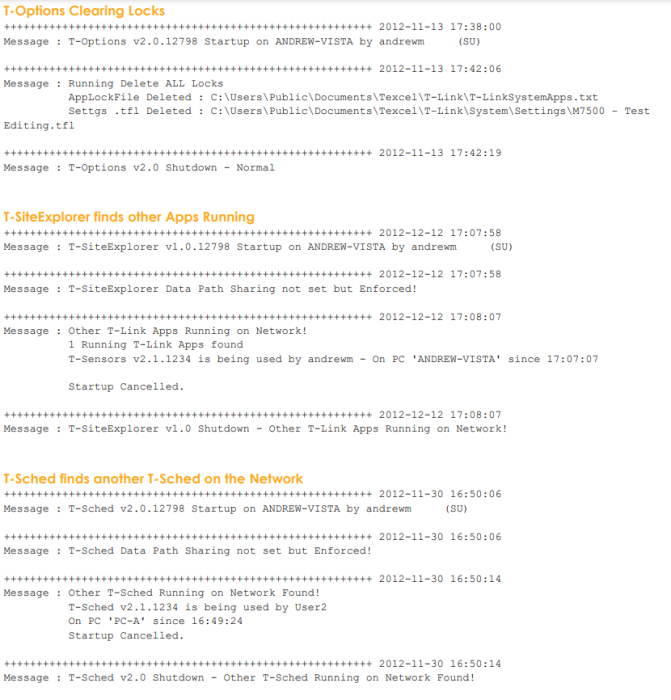
In certain limited situations T-Suite applications will not run when other T-Suite applications are running at the same time. This only affects T-Sched and T-SiteExplorer:
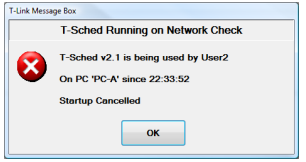
■ Only one T-Sched can be run in the T-Link Data Path (on any PC) at a time
If T-Sched is running on any other PC in the same Data Path you will get this message when you try to start the second copy of T-Sched:
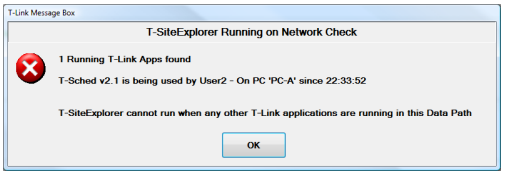
■ T-SiteExplorer requires that no other T-Suite Application is running at the same time
T-SiteExplorer can move, rename, delete or import data, so any other running application on any PC on the network will cause T-SiteExplorer to abandon startup:
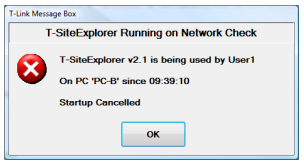
And no other T-Suite application will start if T-SiteExplorer is running in the Data Path.
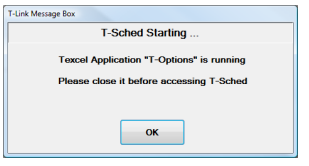
T-Suite Apps won’t start if another T-Suite App is running on the Same PC
■ This happens with or without Data Sharing
There is one exception here in that T-Link will run if T-Sched is running, BUT in a limited ‘Reports Only’ mode i.e. only the Report Button will be enabled.
File Locking
When data is retrieved T-Link or T-Sched will lock the file/s it is writing to before the data is written and unlock them after the data is written, to prevent another T-Link or T-Sched writing to that data file at the same time.
This process is usually pretty quick, and mostly you will see nothing, or a ‘lock message’ like this flashes past while you are retrieving:
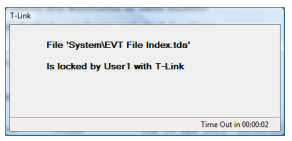
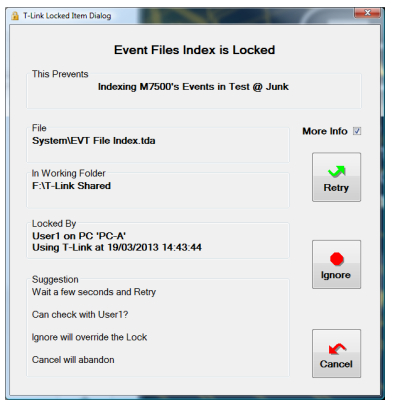
If the file remains locked for more than 5 seconds (time out counted on the ‘lock message’), you get this window:
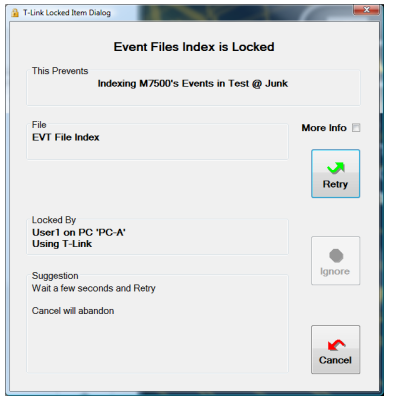
with ‘More Info’ if you want it:
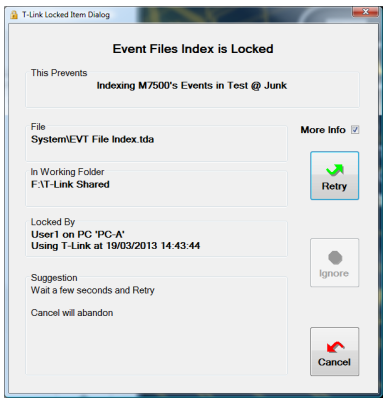
Initially the file name, and the user and PC that locked the file is shown.
The ‘More Info’ Tickbox Shows
- Full details on the file, so you can confirm the Shared Data Path (working folder)
- The date and time at the file was locked
This Prevents
The box at the top is ‘This prevents’ explains what part of the process is being help up by the lock
There is also a Suggestion
■ It is always worth reading and following the suggestion
From this window you have initially only two options
Cancel
This abandons what you are doing.
You will have to confirm the cancel:
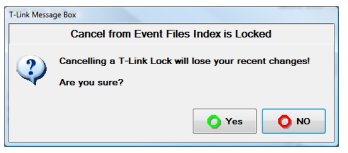
■ This can result in a loss of data
Retry
This simply restarts the timeout and has another go at locking the file. In most cases this will work. Perhaps the information under Locked By will give you an indication of how long it is worth waiting.
You can retry as many times as you want.
Once you have retried once, you get the opportunity to Ignore, and an updated Suggestion!
One of the suggestion is usually to check with the person identified at ‘Locked By’.
If you click Ignore, you will have to confirm this question:
What does T-Sched do when it finds a Lock?
Clearly there is no person to manage this Ignore, Retry, Cancel process.
T-Sched automatically doubles the timeouts.
T-Sched has an inherent retry process in its task schedule, so it will safely retry any task abandoned by a locking process.
Other Multi-User Processes
Monitor History Files Identify PC and User in Monitor Activity Reports
All connections to a monitor are logged into the Monitor History and identify the date, time and action
being undertaken E.g.:
2012-12-17 17:42:30 – Connecting – Configure Custom FW:2.25
In a Shared Data Path, the PC and User name are also identified:
2012-12-19 19:16:10 – Connecting – Configure Custom FW:2.29 PC: ANDREW-VISTA User: andrewm
■ These details are available in Monitor Activity Reports
Reporting Process is Read only with data files
T-Link 2.2 updates the reporting process, so that no changes are recorded in the reported data files. This allows any user to run any type of report without affecting data retrieval by other users.
Network Path and Mapped Drive Awareness
If a PC refers to a shared path by a different name, usually because of mapped network drive identifiers, T-Link (or T-Sched) will identify this path correctly by its full UNC path.
This prevents the old “Event Files are NOT all in Working Local Path – Fix Them?” messages, and the related waveform reporting problems when for example: User A may see the T-Link Data Path as “\\Blast Data\T-Link”; while User B sees it as “T:\T-Link”; and these are the same place.
Shared System LOG File for Easy Analysis
T-Suite creates a Shared System LOG File for all Network Users in a Shared Data Path.
All T-Suite Applications from all users log their activity to this LOG File.
This greatly simplifies understanding activity across a network.
Some Details on the Shared System LOG File
The Shared System LOG file is found in the Shared Data Path and is called ‘T-LinkSystemLOG.txt’, and can be opened with Notepad.
■ Do not edit your T-LinkSystemLOG.txt file
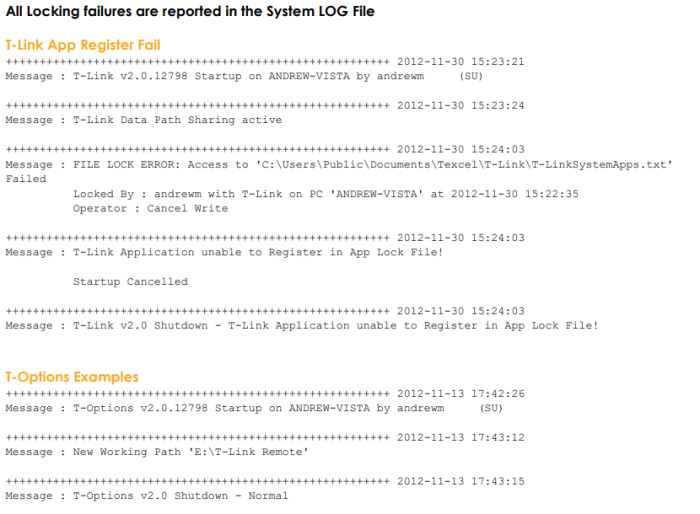
Shared System LOG Example Entries
The System LOG File records all T-Suite Applications starting up and shutting down
It also shows if Data Sharing is Active and the current Data Path, if it has been moved:

Further Assistance
If you need any further assistance, please contact Texcel:
Phone: +61-7-3237 8111
Email: team@texcel.com.au
